Recent Innovations in image encryption techniques: A Review


Various digital images from several fields on the internet are facing various risks like a content leak, illegal access etc. To ensure the safe and private transfer of photos over the internet, image encryption is essential to resolving this problem. Many research and engineering institutions are working on developing a secured image encryption algorithm that securely transmits any image. There are various image encryption methods and techniques, in this paper, we will discuss important image encryption techniques and give a brief review of different image encryption techniques with their comparison. The paper concludes by discussing highlighting future challenges. In this blog, The methods and architectures of several picture encryption solutions that offer security and privacy are examined.
Optical image encryption
Due to enhancement in digital computer networks, storage devices, and digital content, digital images have been considerably used in various fields .In recent days security is one of the core areas to be researched. Image encryption is a method to generate high-quality images to keep information safe and secure. As images are transmitted over public networks, they have a high risk of various security threats like eavesdropping, duplication and illegal modification, etc. hence the security of images in an effective manner and has gained much attention in past few years.
Data Security techniques
Information security is classified into two types namely information hiding methods and cryptography further the information hiding methods are divided into watermarking and steganography.
Fig. 1. Types of security techniques
Figure 1 shows the type of security techniques for information such as text image, video etc .
Applications of Image Security
As in the current scenario, information security is increasing day by day. Image Watermarking image encryption, image hiding uses are applicable in many areas such as defence data security systems, medical image transmission, Video data monitoring, online traffic controlling and many more. To store and transmit the data securely, cryptographic methods or tools are used widely for ensuring all the goals of security. Numerous metrics, including histogram analysis, mean value analysis, key space analysis, adjacent pixel correlation analysis, encryption speed, number of pixels change rate (NPCR), and unified average changing intensity (UACI) tests, can be used to evaluate the efficacy of an image encryption algorithm.
Cryptography
Data encryption and decryption are carried out using procedures known as symmetric and asymmetric key encipherment. The first approach encrypts and decrypts data using a single secret or private key that is shared by the sender and the recipient. In the latter case, the data is encrypted using a public key and decrypted using a private key. It uses a one-way trapdoor function (OWTF) to generate secure public and private key pairs. Asymmetric schemes are more secure as it does not face the problem of key distribution as in the case of symmetric schemes. But latter method is time-consuming and requires high computations.
Image Encryption techniques
An efficient technique for safely transmitting photos via digital platforms is image encryption. To comprehend the utilisation of picture encryption approaches in technical applications, we address them in this research along with their functioning methodology. There are two types of picture encryption techniques: optical, spatial compression, and transform.
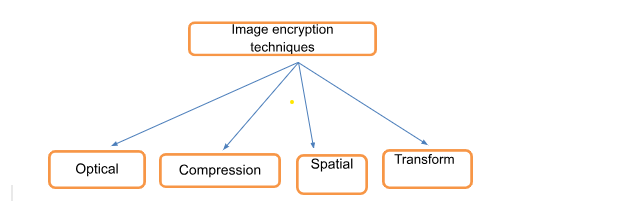
Fig. 2. Image encryption techniques.
Visit for more information related to course for this: https://www.ncuindia.edu/programme/b-tech-cse-with-specialization-in-artificial-intelligence-and-machine-learning
Authored By
Ms. Bhavana Sharma
Assistant Professor
CSE Department
LinkedIn profile:https://www.linkedin.com/publicprofile/
settings?trk=d_flagship3_profile_self_view_public_profile
Broad research areas: Cyber security, Machine learning, Image processing














